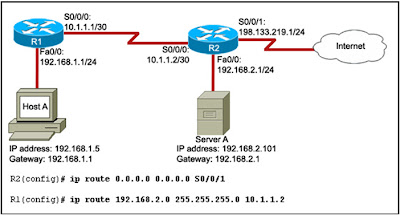
- What is the purpose of the routing process?
- Which service team in an ISP is responsible for determining if the new customer has hardware that will support the new WAN connection and if new WAN circuits need to be installed?
- Which statement describes a route that has been learned dynamically?
- What needs to be configured on a router to ensure that when the router receives a packet with an unknown destination, the router will forward it to the next hop?
- Which routing protocol facilitates the exchange of routing information between different autonomous systems?
- Which routing protocol excludes the subnet information from routing updates?
- Why is the OSI model useful in network design and assessment?
- Refer to the exhibit. Which three IP addresses could be assigned to the hosts? (Choose three.)
- A user is attempting to do an http://www.cisco.com/ without success. Which two configuration values must be set on the host to allow this access? (Choose two.)
- Refer to the exhibit. The network administrator must set up a network with two subnets. In network A, the network administrator selects the network address 192.168.1.128/26. Which address combination should the administrator select in network B to accommodate the same number of hosts as in network A?
- How many host addresses may be assigned on each subnetwork when using the 130.68.0.0 network address with a subnet mask of 255.255.248.0?
- Refer to the exhibit. What two addresses are the broadcast addresses for network A and network B? (Choose two.)
- Refer to the exhibit. A network administrator is troubleshooting the serial connection between R1 and R2. There is no communication between R1 and R2. Based on the output of the show ip interface brief command, what is the cause of the problem?
- What is a feature of PAT?
- Refer to the exhibit. The PC tries to ping router B at 192.168.2.2, but the ping fails. What is the problem?
- The show ip route command was executed on one of the routers shown in the graphic and the following output was displayed:
- Refer to the exhibit. R1 and R2 are configured with the commands that are displayed. All interfaces are properly configured, but neither router is receiving routing updates. What two things can be done to solve the problem? (Choose two.)
- Refer to the exhibit. Static routes have been configured on all routers in the network. PC2 can communicate with PC1 but not with PC3. What should be done to remedy the problem?
- Refer to the exhibit. A technician has been assigned to configure RIPv2 as a routing protocol on the network. Users who are connected to the LAN network on router R3 can ping both S0/0/0 and S0/0/1 interfaces on R1 but are not able to ping the LAN network that is attached to R1. What could be the possible cause of the problem?
- Different hosts connect to the same switch port at different times. If the switch port is configured with dynamic port security, how does it process the MAC addresses?
- Refer to the exhibit. A ping 192.168.1.20 command is issued on workstation A to determine if workstation B can be reached. What two events will occur if this command is successful? (Choose two.)
- Refer to the exhibit. What two conclusions can be drawn about router RTB? (Choose two.)
- If the configuration register is currently set to 0x2102, what is the first action that a router will take after the bootstrap program loads successfully?
- Refer to the exhibit. A network administrator is unable to ping H1 from the router and is checking the cabling along the network. Which segment is incorrectly cabled?
- Refer to the exhibit. A user who is connected to RTA is trying to telnet to RTB, but the connection is failing. Based on the output of the show running-config command on router RTB, why is the Telnet session failing?
- Refer to the exhibit. What will be the effect of the configuration commands if entered on R2?
- An administrator wishes to protect a router by encrypting the console access password noaccess. Which command should be used?
- Refer to the exhibit. The network administrator needs to configure the Fa0/0 interface of RTB so that hosts from RTA can connect to the server that is attached to RTB. Which two commands will the administrator use to accomplish this task? (Choose two.)
- Refer to the exhibit. While configuring the serial interface of a router, the network administrator sees the highlighted error message. What is the reason for this?
- Refer to the exhibit. The network administrator of the building in the graphic needs to choose the type of cable best suited to add ServerB to the network. Which cable type is the best choice?
- In a structured cable system, which term describes the cable that connects the wall jack in the user work area to the patch panel in the wiring closet?
- What is the maximum unrepeated distance set by industry standards for UTP cable?
- Which statement is true about the reverse lookup DNS zone?
- Which statement describes a feature of TCP?
- Which transport layer protocol will allow segments to be exchanged between two hosts with low overhead and no mechanism for retransmission?
- A company is developing an Internet store for its website. Which protocol should be used to transfer credit card information from customers to the company web server?
- Which statement is correct about the proxy support that is offered by the HTTP protocol?
- In the URL http://dev.cisco.com/wwwdocs/procedures.htm, what is identified by wwwdocs?
- A network administrator must access a remote Linux server at the branch office to troubleshoot a web service configuration issue. Which secure protocol would be used?
- When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
- Which technology is used for WAN connections and delivers up to 1.544 Mb/s of symmetrical bandwidth?
- Refer to the exhibit. A new branch office has been added to the corporate network and a new router is to be installed to allow branch office users to access the database server at headquarters. How should the serial 0/0/0 interface of the new branch office router be configured to connect to the headquarters router?
- The command copy tftp running-config has been entered on the router. What will this command do?
- A company functions from Monday to Friday each week. Their backup strategy calls for full backups each Friday night, with differential backups on all other weekday nights. If an administrator is asked to restore a server hard drive to its Wednesday morning state, how many backups must be used?
- What is a characteristic of Syslog?
to select the paths that are used to direct traffic to destination networks
planning and provisioning
It is automatically updated and maintained by routing protocols.
a default route
BGP
RIPv1
It divides networking communications into multiple processes that are smaller and more manageable.
192.168.88.9
192.168.88.12
192.168.88.14
192.168.88.12
192.168.88.14
DNS server
default gateway
default gateway
192.168.1.64 255.255.255.192
2046
Network A broadcast address 192.168.1.47
Network B broadcast address 192.168.1.207
Network B broadcast address 192.168.1.207
There is a misconfiguration of IP addresses.
It allows multiple hosts on a single LAN to share globally unique IP addresses.
The address of the PC is on the wrong subnet
C 192.168.4.0/24 is directly connected, Serial0/0
R 192.168.5.0/24 [120/1] via 192.168.4.2, 00:00:19, Serial0/0
R 192.168.1.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
R 192.168.2.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
C 192.168.3.0/24 is directly connected, Serial0/1
From which router was this command executed?
C
Configure the routing protocol on R1 for network 10.0.0.0.
Configure the routing protocol on R2 for network 10.0.0.0.
Configure the routing protocol on R2 for network 10.0.0.0.
Reconfigure the second static route with the exit interface S0/0/1.
The network 172.16.10.0 command was not issued when RIP was configured on router R1.
The addresses are dynamically learned and stored in the address table.
Workstation A will send an ICMP echo request message to workstation B.
Workstation B will send an ICMP echo reply message to workstation A.
Workstation B will send an ICMP echo reply message to workstation A.
Router RTB is connected to a Cisco 1841 router.
The IP address of the router interface that is connected to router RTB is 192.168.2.6.
The IP address of the router interface that is connected to router RTB is 192.168.2.6.
load the IOS from flash
Segment D
No password has been configured on the VTY lines.
The user will be able to console into R2 using the password cisco.
Router(config)# service password-encryption
RTB(config-if)# no shutdown
RTB(config-if)# ip address 192.168.102.97 255.255.255.252
RTB(config-if)# ip address 192.168.102.97 255.255.255.252
The network administrator has attempted to configure the serial interface with a broadcast address.
fiber optic
horizontal cable
100 meters
It resolves an IP address to a fully qualified domain name.
It acknowledges the receipt of packets.
UDP
HTTPS
It filters unsuitable web content.
the folder where the requested resource is stored
SSH
circuit switched
T1 line
branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.21 255.255.255.240
branch_23(config-if)# no shutdown
copy the configuration file from a server to RAM
2
It enables devices to send information to a daemon that runs on a management station.